27 Feb 2025

In the high-stakes worlds of traditional finance and digital asset management, securing transactions against sophisticated threats is non-negotiable. A recent breach at a crypto exchange—where attackers exploited a multisignature (multisig) wallet to siphon $1.4 billion in ETH through a deceptive user interface (UI)—underscores the risks. Yet, the time-tested maker-checker framework, a cornerstone of fiat money transfers, offers a resilient blueprint that adapts seamlessly to digital assets. Even if a hacker compromises the maker’s email and targets checkers directly, a well-designed process can still foil the attack.
The Crypto Breach: A Digital Lesson
The exchange relied on a multisig wallet, likely requiring approvals from a subset of senior executives (e.g., 3 out of 5) to access a cold storage facility and authorize a transaction. The attacker succeeded by presenting a falsified UI, tricking approvers into signing a malicious transaction. This exposed a critical gap in procedural oversight: without a structured initiation and validation process, the system leaned too heavily on the UI’s apparent trustworthiness—leaving it vulnerable to exploitation.
Fiat Parallels: Handling a Compromised Maker
In traditional investment fund operations, a similar vulnerability arises with fiat wire transfers—consider a $1.4 million outward payment. Suppose a hacker breaches the maker’s email (e.g., a treasury staff member) and sends a fraudulent request to the checkers: “Wire $1.4M to account XYZ for vendor payment.” In a weak system, this might succeed—but a robust maker-checker process intervenes, even under compromise. Here’s how:
• Maker’s (Compromised) Action: The hacker, using the maker’s hacked email, initiates the transfer in the bank portal and emails checkers:“Approve $1.4M to XYZ, ref: 12345.”
• Checker’s Independent Role: Approvers don’t rely solely on the email. Policy mandates:
o Cross-Check: Verify transaction details (payer, payee, purpose, supporting documents) in the fund’s online banking portal against a trusted source—e.g., an internal log or original client instructions (not the email).
o Callback Verification: Call the client or an authorized contact (e.g., the vendor or a manager) to confirm: “Did you request $1.4M to XYZ?”
• Outcome: The callback exposes the fraud—perhaps the vendor denies the invoice, or the manager flags it as unauthorized. The checkers halt the transfer, despite the compromised email.
This succeeds because the checker’s diligence—especially the out-of-band phone call—operates independently of the hacked email channel. The hacker’s control over the maker’s account doesn’t extend to the client or the checker’s verification steps.
Adapting to Digital Assets: The Hacked Email Scenario
Though the traditional finance scenario differs from digital asset environments, the same logic applies to the crypto exchange’s $1.4 billion hack—and to digital asset funds broadly. Imagine a hacker compromises the maker’s email and sends a fake request to the checkers. Here’s how a fortified maker-checker process handles it:
• Transaction Initiation: An operations team member (maker) typically proposes a transfer in the multisig interface—e.g., “Move 50 ETH to 0xABC for liquidity”—and emails approvers with the hash.
• Hacker’s Move: : The hacker, controlling the maker’s email, sends a fraudulent email to checkers: “Approve 500 ETH to 0xXYZ, hash: 0x456…,” and manipulates the multisig UI to match.
• Checker’s Defense: Approvers follow a strict protocol:
o Cross-Check: Access the multisig interface via a trusted bookmark (not an email link) and compare the UI’s details (500 ETH to 0xXYZ, hash: 0x456…) to an independent reference—e.g., a secure internal dashboard or the maker’s usual pattern (routine 50 ETH transfers).
o Callback Verification: Call the maker or a designated authority (e.g., “Did you intend 500 ETH to 0xXYZ, or was it 50 ETH to 0xABC?”) using a pre-verified phone number, not one from the email.
• Thoughts: Since approvers at this exchange are senior executives, they may not verify every daily transaction’s details. A sub-delegated checker (e.g., an assistant or administrator) can act on their behalf, making the maker-checker mechanism feasible. Even for minor amounts—where a hacker might use a small sum to evade scrutiny—any transaction involving a senior approver touching the core wallet warrants strict verification.
• Resolution: The callback likely exposes the fraud—the maker confirms the legitimate intent (50 ETH to 0xABC), or the authority flags the anomaly. The UI mismatch triggers rejection, even if the email and UI align perfectly under the hacker’s control.
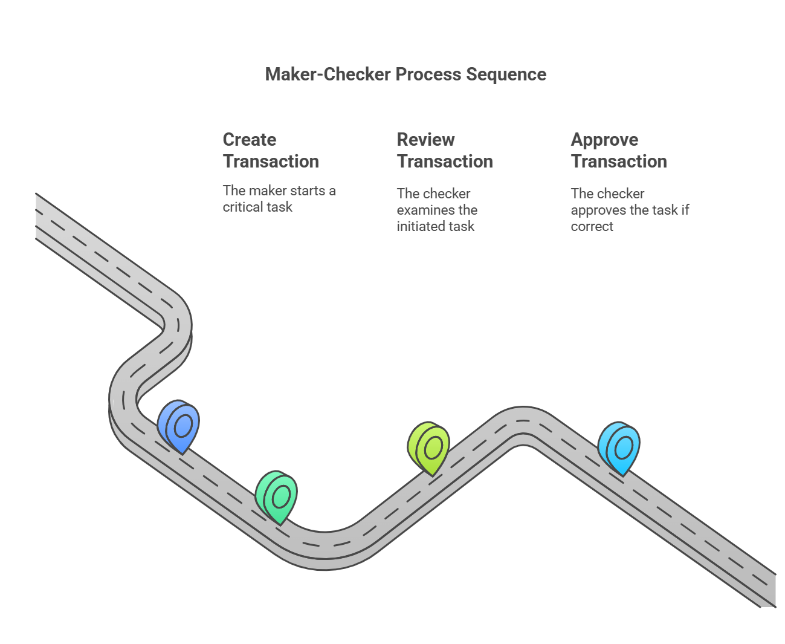
Why It Holds Up
This process succeeds in both fiat and digital contexts because:
• Independent Channels: The callback bypasses the hacked email, relying on a separate, trusted communication line—clients in fiat, the maker or a supervisor in crypto.
• Separation of Duties: Checkers don’t assume the maker’s request is valid; they verify it externally. A compromised maker can’t deceive an alert checker.
• Behavioral Cues: In the crypto case, a sudden jump from 50 ETH to 500 ETH or an unfamiliar address prompts scrutiny—especially for a cold wallet meant for rare, deliberate moves.
Had the exchange implemented this, the $1.4 billion hack might have been thwarted. Even if the hacker spoofed the maker’s email, a callback—“Did you request this massive transfer?”—would have unraveled the ruse, as the real maker or authority would deny it. Each step adds a barrier to deter attacks; no single solution guarantees total protection.
Cold Wallet Discipline: Fiat-Inspired Precision
Cold wallets, like bank vaults, demand meticulous handling—whether safeguarding $1.4 million in fiat or $1.4 billion in ETH. A maker-checker process enforces this:
• Fiat Lesson: A $1.4M wire requires a client callback; a 50 ETH transfer merits a maker confirmation call.
• Digital Edge: The multisig hash provides a verifiable fingerprint, allowing checkers to confirm intent against the UI, even if the maker’s email is hacked.
This hybrid—real-world verification paired with blockchain precision—ensures administrators don’t rely solely on technical safeguards (vulnerable to UI spoofing) but reinforce them with human oversight.
Implications for Fund Administrators
Across fiat and digital assets, the threat persists: a hacked insider channel (like email) can initiate fraud. The maker-checker framework, proven in banking, adapts to crypto with minimal friction. It’s not foolproof—hackers might escalate to phone spoofing—but it forces them to breach multiple layers, not just one. For a $1.4 million wire or a $1.4 billion ETH stash, the defense remains consistent: split duties, verify intent, and confirm independently. As independent third parties, fund administrators review each case objectively, adding another layer of resistance to compromise.
A Practical Blueprint
To implement this resilient approach:
• Policy: Mandate maker notification via email, checker cross-checks against the UI, and a callback to the maker or authority for all high-value transfers. A tailored SOP should clearly outline roles and duties for asset transfers.
• Training: Teach staff to flag anomalies (e.g., unusual amounts or addresses) and use secure, pre-verified contact methods.
• Testing/Audit: Simulate hacks—including a compromised maker email—to ensure checkers catch discrepancies.
In an industry balancing speed and security, this process—rooted in fiat’s real-world wisdom and tailored to digital assets—offers a pragmatic shield. The $1.4 billion hack, like a foiled wire fraud, proves technology needs human backup. Even if a hacker hijacks the maker’s email, the four-eyes principle could prevent the loss.